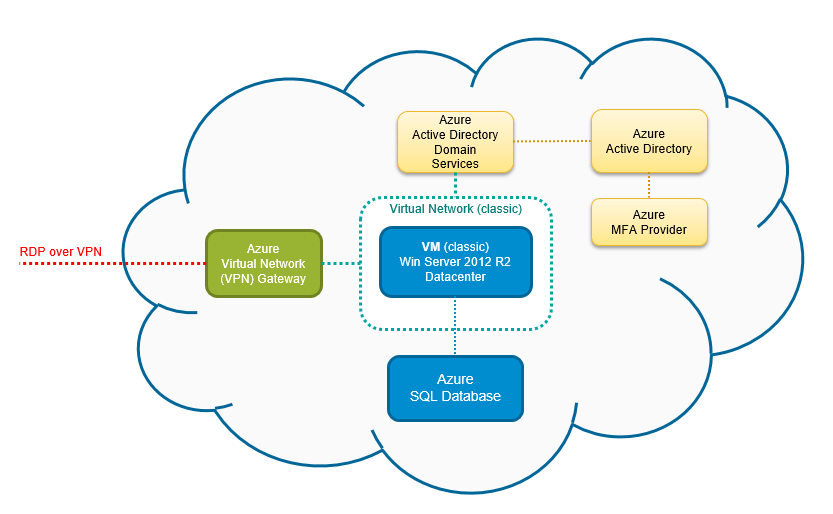
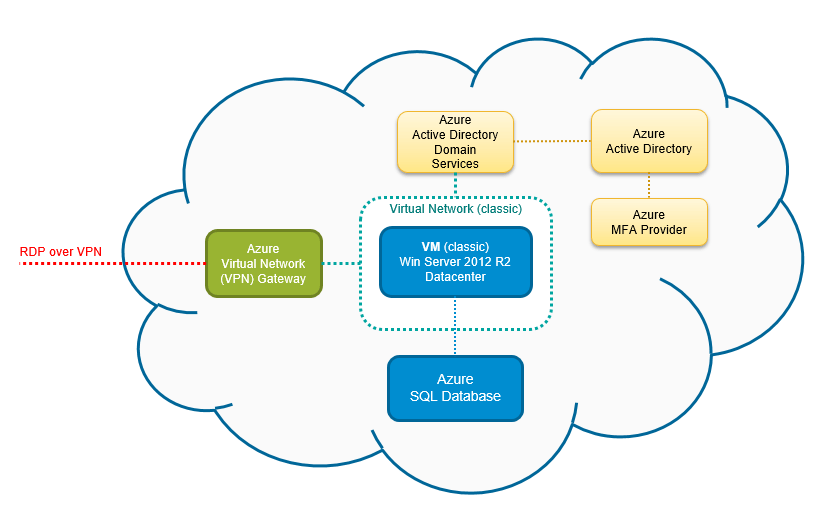
Azure Virtual Network : 7 Powerful Insights You Must Know
Welcome to your ultimate guide on Azure Virtual Network (VNet)—your gateway to building secure, scalable, and high-performance cloud environments in Microsoft Azure. Whether you’re a cloud architect, network engineer, or IT decision-maker, understanding VNet is essential for mastering cloud networking.
What Is Azure Virtual Network (VNet)?

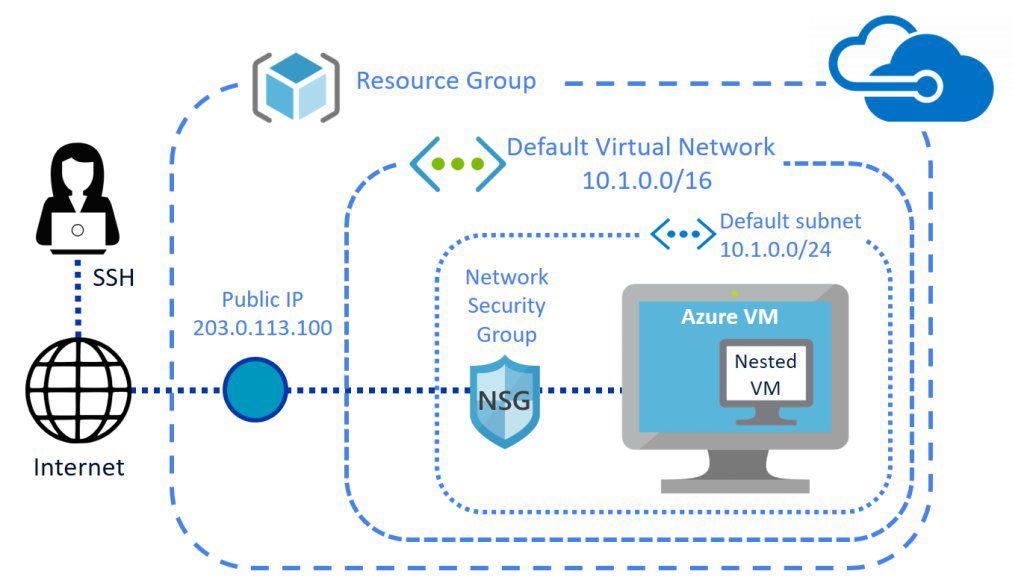
Azure Virtual Network (VNet) is the fundamental building block for private networks in Microsoft Azure. It enables Azure resources to securely communicate with each other, the internet, and on-premises networks. Think of it as your own private segment of the cloud—fully isolated, customizable, and under your control.
Core Definition and Purpose
At its core, an Azure Virtual Network (VNet) is a representation of your own network in the cloud. It provides logical isolation for your Azure resources, allowing you to define IP address ranges, subnets, security policies, and routing rules. VNets act as a security boundary and enable communication between virtual machines (VMs), apps, and services within Azure.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
- Provides private IP addressing using IPv4 (and IPv6 in select regions)
- Enables segmentation via subnets
- Supports network security groups (NSGs) and firewalls
“Azure Virtual Network is the foundation of Azure networking—everything connects through it.” — Microsoft Azure Documentation
How VNet Fits Into the Azure Ecosystem
VNet isn’t just a standalone service—it’s the central hub that connects various Azure components. From Azure App Services and Azure Kubernetes Service (AKS) to Azure Virtual Machines and Azure SQL Managed Instance, most PaaS and IaaS services rely on VNet integration for secure access.
- Enables private connectivity to PaaS services via VNet service endpoints or private links
- Integrates with Azure ExpressRoute and VPN Gateway for hybrid connectivity
- Supports multi-tier application architectures (e.g., web, app, and database tiers in separate subnets)
Azure Virtual Network (VNet): Key Features and Capabilities
The power of Azure Virtual Network (VNet) lies in its rich set of features designed to support enterprise-grade networking. These capabilities make it possible to design complex, secure, and resilient network topologies in the cloud.
IP Addressing and Subnetting
When you create a VNet, you define one or more private IP address spaces using CIDR notation (e.g., 10.0.0.0/16). Within this space, you can create subnets to organize and isolate different types of workloads.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
- Supports both IPv4 and IPv6 (dual-stack in preview)
- Subnets allow granular control over traffic flow and security policies
- Custom DNS settings can be applied at the VNet level
For example, you might allocate 10.0.1.0/24 for web servers, 10.0.2.0/24 for application servers, and 10.0.3.0/24 for databases—each with distinct security rules.
Network Security Groups (NSGs)
NSGs are fundamental to securing traffic within and to your VNet. They act as virtual firewalls, allowing or denying traffic based on source/destination IP, port, and protocol.
- Can be applied to subnets or individual network interfaces
- Support both inbound and outbound rules
- Default rules provide basic connectivity while allowing customization
For instance, you can block all inbound traffic to a database subnet except from the application tier subnet, enhancing security through segmentation.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
User-Defined Routing (UDR)
By default, Azure handles routing within VNets automatically. However, User-Defined Routes let you override this behavior to direct traffic through virtual appliances (like firewalls or IDS/IPS systems) or across complex network topologies.
- Define custom routes using route tables
- Route traffic to virtual network appliances (VNAs)
- Enable forced tunneling to on-premises networks
This is especially useful in scenarios requiring traffic inspection or compliance with regulatory standards.
Designing Your Azure Virtual Network (VNet) Architecture
Designing an effective Azure Virtual Network (VNet) requires careful planning. A well-architected VNet supports scalability, security, and performance while minimizing complexity and cost.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Single vs. Multi-VNet Topologies
You can start with a single VNet for simplicity, but as your environment grows, a multi-VNet design becomes necessary for isolation and scalability.
- Single VNet: Ideal for small environments or proof-of-concept deployments
- Multi-VNet: Used in production for separating environments (dev, test, prod) or business units
- Peering connects VNets for seamless communication
For example, a financial institution might use separate VNets for customer-facing applications, internal systems, and data analytics platforms.
Hub-and-Spoke Model with VNet Peering
The hub-and-spoke model is a widely adopted architecture in Azure. In this model, a central “hub” VNet provides shared services like firewalls, DNS, and connectivity to on-premises networks, while “spoke” VNets host workloads.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
- Spoke VNets peer with the hub for access to shared services
- Transitive routing is enabled via virtual appliances in the hub
- Reduces duplication and improves manageability
This model is recommended by Microsoft and is part of the Azure Hub-Spoke Architecture.
Address Space Planning and Overlap Avoidance
One of the most critical aspects of VNet design is IP address planning. Poor planning can lead to address space conflicts, especially in hybrid scenarios.
- Use non-overlapping CIDR blocks across VNets and on-premises networks
- Reserve large enough address spaces for future growth (e.g., /16 for major segments)
- Leverage tools like Azure IP Address Manager (in preview) for tracking
For example, avoid using 192.168.0.0/24 if your corporate network already uses it—opt for 10.x.x.x ranges instead.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Connecting Azure Virtual Network (VNet) to On-Premises Networks
Hybrid connectivity is a cornerstone of modern cloud strategies. Azure Virtual Network (VNet) supports multiple methods to connect your cloud resources to on-premises data centers.
Site-to-Site (S2S) VPN
A Site-to-Site VPN creates an encrypted tunnel over the public internet between your on-premises VPN device and the Azure VPN Gateway.
- Cost-effective for small to medium bandwidth needs
- Easy to set up and manage
- Supports failover with active-active gateways
It’s ideal for organizations that need secure, persistent connections without investing in dedicated circuits. Learn more at Azure Site-to-Site VPN Documentation.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Azure ExpressRoute
ExpressRoute provides private, high-speed connectivity between your on-premises infrastructure and Azure through a connectivity provider.
- Bypasses the public internet for lower latency and higher reliability
- Supports bandwidths up to 100 Gbps
- Meets strict compliance and data sovereignty requirements
Industries like healthcare and finance often choose ExpressRoute for mission-critical applications. It integrates directly with VNet via peering locations.
Point-to-Site (P2S) VPN
Point-to-Site VPN allows individual devices to connect securely to a VNet over SSL/TLS. This is perfect for remote workers or developers accessing cloud resources.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
- No need for a corporate VPN device
- Supports L2TP/IPsec and OpenVPN protocols
- Can authenticate users via Azure AD (in preview)
P2S is often used alongside S2S for flexibility—site-to-site for data centers, point-to-site for mobile users.
Securing Your Azure Virtual Network (VNet)
Security is paramount in cloud networking. Azure Virtual Network (VNet) offers multiple layers of protection to safeguard your data and applications.
Network Security Groups (NSGs) vs. Azure Firewall
While NSGs provide basic layer 3 and 4 filtering, Azure Firewall is a managed, cloud-native firewall service offering advanced capabilities.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
- NSGs: Best for simple allow/deny rules based on IP and port
- Azure Firewall: Supports FQDN filtering, threat intelligence, and SNAT/DNAT rules
- Can be deployed in a hub VNet for centralized inspection
For example, use NSGs to restrict RDP access to specific subnets, and Azure Firewall to block malicious domains across all VNets.
DDoS Protection in Azure VNet
Distributed Denial of Service (DDoS) attacks can cripple your applications. Azure offers DDoS Protection plans to safeguard your VNet resources.
- Basic protection is enabled by default for all public IPs
- Standard plan provides adaptive tuning, real-time telemetry, and mitigation reports
- Integrates with Azure Monitor and Security Center
Enabling DDoS Protection Standard is a best practice for internet-facing applications. More details at Azure DDoS Protection Overview.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Private Endpoints and Service Endpoints
These features enhance security by limiting public exposure of Azure services.
- Service Endpoints: Extend your VNet identity to Azure PaaS services over the Microsoft backbone
- Private Endpoints: Assign a private IP from your VNet to a PaaS resource, making it accessible only from within the VNet
- Both prevent data exfiltration and reduce attack surface
For example, use Private Endpoints to access Azure Storage or Azure SQL without exposing them to the public internet.
Monitoring and Troubleshooting Azure Virtual Network (VNet)
Even the best-designed networks require monitoring and troubleshooting. Azure provides powerful tools to gain visibility into your VNet performance and health.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Azure Network Watcher
Network Watcher is the primary tool for monitoring, diagnosing, and logging network issues in Azure.
- Provides IP flow verify to check if traffic is allowed or blocked by NSGs
- Offers connection troubleshoot to diagnose VM connectivity issues
- Enables packet capture for deep packet inspection
It’s essential for validating security rules and diagnosing connectivity problems. Learn how to use it at Azure Network Watcher Documentation.
Flow Logs and Traffic Analytics
Enable VNet flow logs to capture information about IP traffic flowing through your NSGs.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
- Logs include source/destination IP, port, protocol, and action (allow/deny)
- Integrated with Azure Monitor and Log Analytics
- Traffic Analytics processes flow logs to provide insights into traffic patterns and anomalies
This is invaluable for security auditing, compliance, and identifying unexpected traffic flows.
Connection Monitor and Metrics
Connection Monitor lets you proactively test connectivity between resources.
- Monitor round-trip time (RTT), packet loss, and reachability
- Test from on-premises to Azure or between Azure regions
- Set up alerts based on performance thresholds
Combined with Azure Monitor metrics, this gives you end-to-end visibility into network performance.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Best Practices for Managing Azure Virtual Network (VNet)
Following best practices ensures your Azure Virtual Network (VNet) remains secure, scalable, and efficient over time.
Implement Role-Based Access Control (RBAC)
Use Azure RBAC to assign granular permissions for managing VNets.
- Avoid giving Contributor access to everyone
- Create custom roles for network administrators
- Use Azure Policy to enforce governance rules
For example, restrict VNet modifications to a dedicated network team while allowing developers to deploy VMs in approved subnets.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Use Azure Policy for Network Governance
Azure Policy helps enforce organizational standards across your VNets.
- Enforce naming conventions for VNets and subnets
- Require NSGs on all subnets
- Prevent public IP addresses on certain VM types
Policies like “Deploy-NSG” or “Allowed-Location” can be assigned at subscription or management group level.
Automate with Infrastructure as Code (IaC)
Manage your VNet configurations using tools like Azure Resource Manager (ARM) templates, Terraform, or Bicep.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
- Ensure consistency across environments
- Enable version control and peer review
- Support CI/CD pipelines for network changes
For example, define your entire hub-and-spoke topology in Terraform and deploy it across multiple regions with minimal effort.
Advanced Scenarios with Azure Virtual Network (VNet)
As your cloud maturity grows, you’ll encounter advanced networking scenarios that require deeper integration with Azure Virtual Network (VNet).
Global VNet Peering and Cross-Region Connectivity
While VNet peering is typically regional, global peering allows VNets in different Azure regions to connect directly.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
- No need for gateways or transit hubs in many cases
- Low-latency, high-bandwidth connectivity
- Supports transitive routing when combined with virtual appliances
This is ideal for disaster recovery setups or multi-region applications requiring tight integration.
Integration with Azure Kubernetes Service (AKS)
AKS clusters can be deployed into existing VNets or have a VNet created automatically.
- Use Kubenet or Azure CNI networking models
- Azure CNI assigns real VNet IPs to pods for better integration
- Enable network policies with Calico or Azure Network Policies
Proper VNet integration ensures secure communication between AKS workloads and other Azure services.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Virtual WAN and VNet Connectivity
Azure Virtual WAN is a networking service that provides optimized and automated branch-to-Azure connectivity.
- Centralized hub for managing multiple VNets and VPN/ExpressRoute connections
- Integrated with Azure Firewall and routing
- Simplifies large-scale hybrid network architectures
It’s especially useful for enterprises with hundreds of branch offices connecting to Azure. Explore more at Azure Virtual WAN Overview.
What is Azure Virtual Network (VNet)?
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Azure Virtual Network (VNet) is a service that provides isolated, private networking environments in Microsoft Azure. It allows Azure resources to securely communicate with each other, the internet, and on-premises networks through customizable IP address ranges, subnets, and security policies.
How do I connect my on-premises network to Azure VNet?
You can connect your on-premises network to Azure VNet using Site-to-Site VPN over the internet or Azure ExpressRoute for private, high-speed connectivity. Point-to-Site VPN is also available for individual remote users.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
What is the difference between VNet peering and VNet gateway?
VNet peering enables direct, low-latency communication between two VNets in the same or different regions without gateways. VNet gateway, on the other hand, is used for connecting VNets to on-premises networks via VPN or ExpressRoute and requires a dedicated gateway resource.
Can I use private IPs for Azure PaaS services like Azure SQL?
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Yes, you can use Private Endpoints to assign a private IP address from your VNet to Azure PaaS services like Azure SQL, Azure Storage, or Azure App Service, making them accessible only within your virtual network.
How do I monitor traffic in my Azure Virtual Network?
Use Azure Network Watcher to monitor and troubleshoot network issues. Enable VNet flow logs and Traffic Analytics to gain insights into traffic patterns, detect anomalies, and audit security rules.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Mastering Azure Virtual Network (VNet) is essential for building secure, scalable, and efficient cloud infrastructures. From designing IP address schemes and implementing hub-and-spoke architectures to securing traffic with firewalls and monitoring performance with Network Watcher, VNet offers the tools you need to succeed in the cloud. By following best practices in governance, automation, and hybrid connectivity, you can ensure your network remains resilient and future-ready. Whether you’re just starting out or managing complex multi-region deployments, Azure Virtual Network (VNet) is your foundation for success.
Azure Virtual Network (VNet) – Azure Virtual Network (VNet) menjadi aspek penting yang dibahas di sini.
Recommended for you 👇
Further Reading: